In the digital age, an organizations’ network and security system (infrastructure) is becoming more complex and challenging, which necessitates various technical and administrative measures to maintain the highest level of confidentiality, integrity, and availability of security grids.
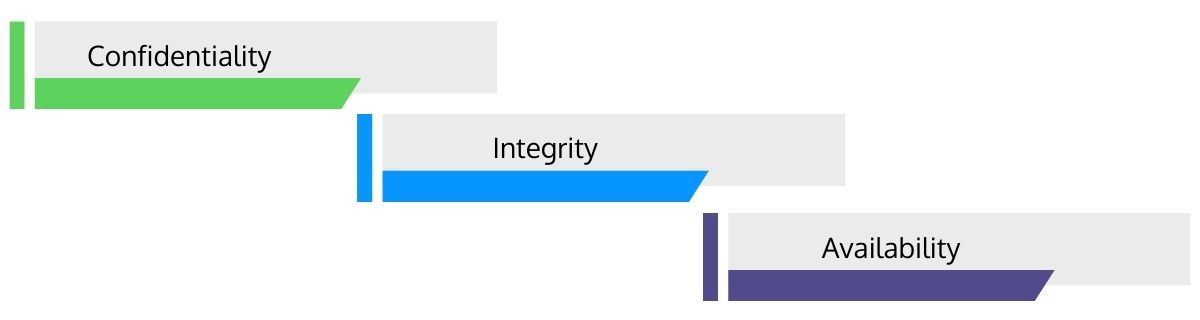
- Confidentiality: A property by the virtue of which a critical system or information is not available or disclosed to unauthorized people, entities, or procedures.
- Integrity: A property associated with the accuracy, completeness, and system consistency regarding regulatory compliance and security.
- Availability: A property of being available and accessible when an authorized entity requires it.
A critical solution is to "employ security auditing", a curative security practice providing the ability to maintain complete control over your mission-critical assets, data, and IT infrastructure by selecting a reputable third-party service provider to perform the function.
This article will discuss security review management in detail including the definitions, features, challenges, and best practices.
Introduction to Security Review Management
"Is your security mature?"
"Is your security program effective?"
Security is about protecting your valuable assets, including intellectual property,strategic plans,sensitive data, and IT auditing in a network.
Security management refers to the set of rules and procedures that IT businesses and organizations use to protect their data assets from threats and security vulnerabilities and the protective measures, which may result in undesired usage of computing systems.
Security review management is a collaborative process that identifies security-related concerns, determines the level of risk associated with these issues, and makes informed decisions for risk mitigation or acceptance.
As businesses perform more of their operations online and use mobile devices, security breaches involving sensitive data are rapidly increasing. A security review process is intended to secure business continuity and minimize potential business damages by limiting the collision of potential security incidents.
Security review management entails various techniques, processes, and practices to safeguard business assets. It focuses on auditing sensitive information or business-critical intellectual property. A security review program can incorporate creating security policies, detecting security risks, and spotting security threats to IT systems. Another critical practice is sharing knowledge about data security best practices with employees.
Key Features of Security Review Management
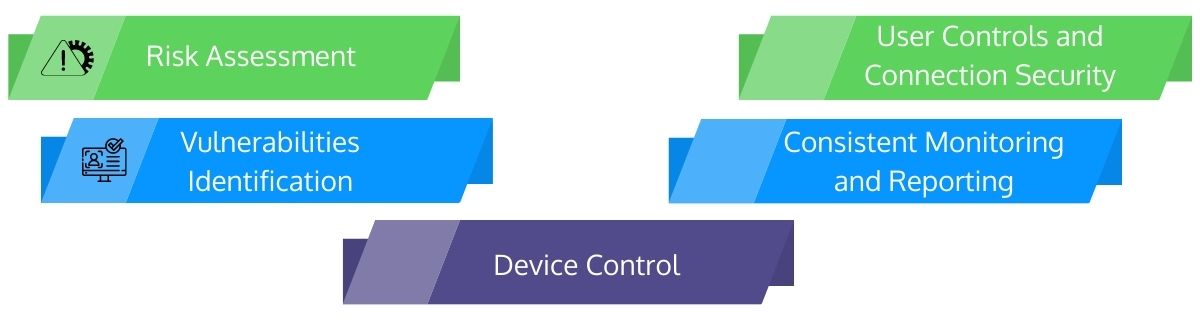
A security review management program must be comprehensive, allowing your firm to exercise security controls across all of your networks, apps, and gateways. It comprises of the following features:
- Risk Assessment
How secure is your security grid? How do you assess security levels? A good security review process can help you determine the risks associated with each new network and or features you add to your suite of security architecture. - Vulnerabilities Identification
A security review management equips the system to notify you about new vulnerabilities. It can also provide adequate time to proactively respond to these vulnerabilities, addressing them before they cause severe damage. - Device Control
With an efficient security assessment, a security team can manage device-level controls, such as which devices have access to your data and how they access it. - User Controls and Connection Security
A secured system assists you in establishing stringent user controls and permissions across all enterprises’ apps. Segmented data accessibility reduces risks and ensures that only authorized users can access your most sensitive information. It also defends certain internal connections for adequate user controls. - Consistent Monitoring and Reporting
A security review management process allows you to monitor traffic and user behavior actively. It gives in-depth information supporting your understanding of trends or patterns and spots potentially suspect activities to help you take preventive actions.
As technology is continuously evolving, your firm must evolve to stay competitive. Thereby, a security system should be updated and expanded regularly. Additionally, the right security review program must be flexible and adaptable, allowing you to scale up and introduce new elements as needed.
Challenges Inside the System
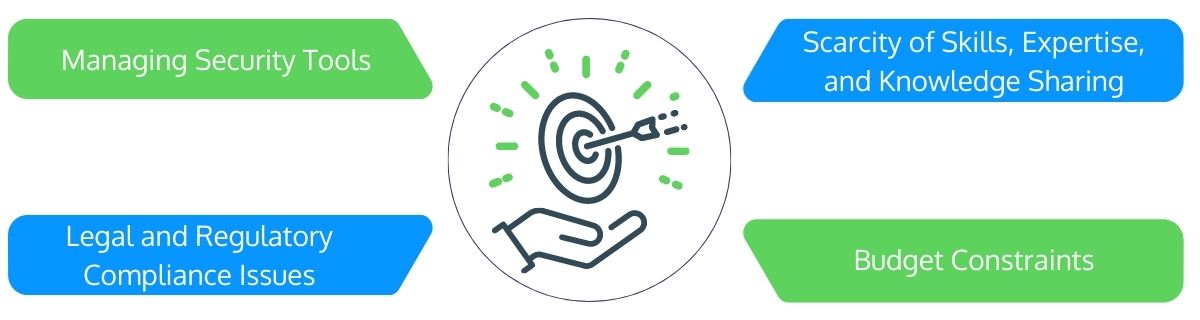
Effective security operations are an essential part of the enterprises’ threat mitigation strategies but grapple with some obstacles as follows:
- Managing Security Tools
As security operations embrace a greater range of security suites, it becomes increasingly challenging to efficiently monitor data accumulated from diverse resources. A typical security management module may include a mix of 20 or more technologies, which can be challenging to track and manage separately.
To successfully manage, monitor, and measure security operations and incident response procedures, a central source and single platform to consolidate all the information are required to attain a holistic view of the complete security environment. - Scarcity of Skills, Expertise, and Knowledge Sharing
Significant concerns include a shortage of skills, competence, and knowledge sharing. A security skills gap and expertise hampers the security team monitoring and managing systems, intervening attacks, slower or failed responses, and the inability to perform correct diagnosis of incidents.
The downside, staff equipped with systems management technologies fail if they have insufficient knowledge about the systems environment to be safeguarded. Knowing too little leads to a failure to perceive problems and an increased risk of responding incorrectly to nonexistent issues. They could receive more false positive and false negative responses. - Legal and Regulatory Compliance Issues
Depending on the industry or geographic area, meeting legal and regulatory compliance standards such as NIST, PCI, GLBA, FISMA, HITECH (HIPAA), GDPR, and industry best practices can significantly impact the firm’s need for a proper security review and management process.
With the GDPR looming, security teams must identify mandatory actions and procedures that must be carried out to comply with the regulations. The legal, financial, and reputational implications and ramifications can be severe if appropriate incident reporting and breach notifications are not provided within the regulatory restrictions. - Budget Constraints
In most companies, budgets are always constrained in some way, shape, or form. Evaluating, monitoring, and managing security operations and incident response is notoriously tricky, so justifying expenditures is always challenging. A clear positive ROI must be forecasted and shown to get an authorization for the expenditure.
Organizations are increasing their investment in cyber security measures in response to the increases in cyber-attacks, but determining the degree of a budget is essential will be exigent.
Conclusion
The security review or audit assists you in identifying security flaws that a hacker, malware, or other threat could take advantage of. Security evaluation teams can typically provide solutions for threat detection and response using threat-modeling programs to extract or modify security postures. They provide a report detailing the security flaws discovered during the audit. Businesses can address vulnerabilities with alleviative solutions allowing them to fine-tune their network and security systems.
On that note, are you looking for an industry partner to boost your security review process or program? Reach out to us for effective security review and IT audit services protecting your organization's sensitive data and reducing your risk of cyberattacks increasing at robotic speed.
BCube Analytics offers a SaaS platform for end-to-end audit management in financial, operational, and security audits, with an emphasis on various aspects of IT security, governance, and review (risk) services. With BCube's "RegStacker" auditors can use this audit management platform to evaluate rules, construct request lists across controls, generate findings, and reconcile management replies.