Security and Privacy
Protecting Your Data with Advanced Security Measures
At BCube Analytics, we prioritize the security and privacy of your data. Our platform incorporates cutting-edge technologies and robust processes to ensure compliance with global standards while maintaining your trust.
Our Security Features
1
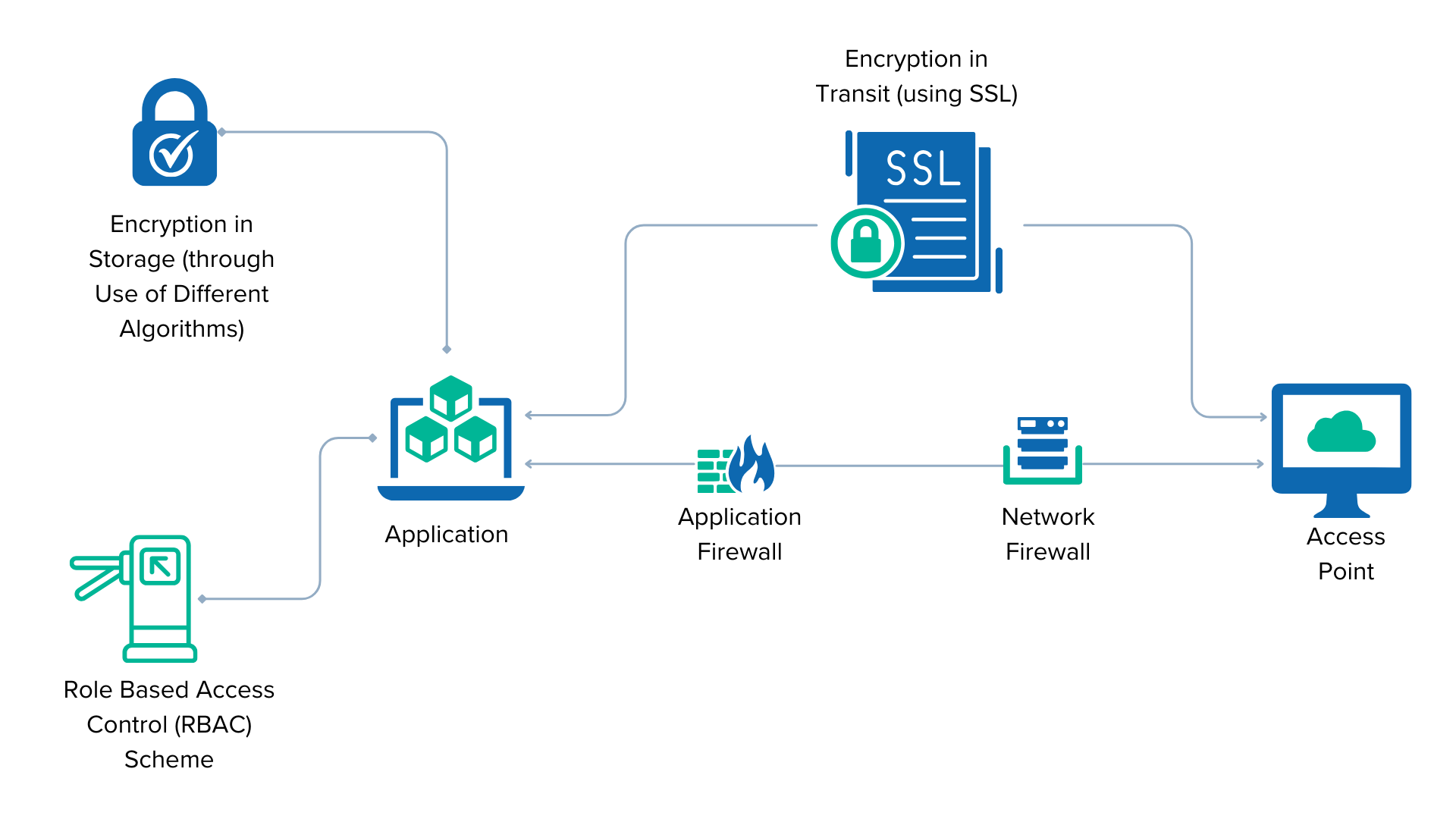
Enterprise-Grade Encryption
- Data is encrypted during transmission (SSL) and at rest using advanced algorithms.
- Passwords are securely hashed and irrecoverable to prevent unauthorized access.
2
Role-Based Access Control (RBAC)
- Enforce granular permissions to ensure users can only access resources relevant to their roles.
- Dynamic permissions matrix to adapt to your organization’s needs.
3
Blockchain for Immutable Records
- Leverage blockchain technology in specific modules to ensure tamper-proof audit trails.
- Enhance data transparency and traceability for compliance audits.
4
Secure Infrastructure
- Hosted in ISO27001 and ISO9001-certified data centers.
- Primary and backup facilities ensure geographic redundancy and business continuity.
- Regular third-party penetration tests and security audits.
5
Real-Time Intrusion Detection
- Employ state-of-the-art intrusion detection systems (IDS) to monitor and mitigate threats.
- Real-time alerting and response for suspicious activities.
Privacy Commitment
Data Ownership and Control
- Your data is always under your control and ownership.
- Backup and export options ensure you retain access to your information.
Data Residency
- Data is stored exclusively in US-based Type IV data centers, ensuring compliance with local regulations.
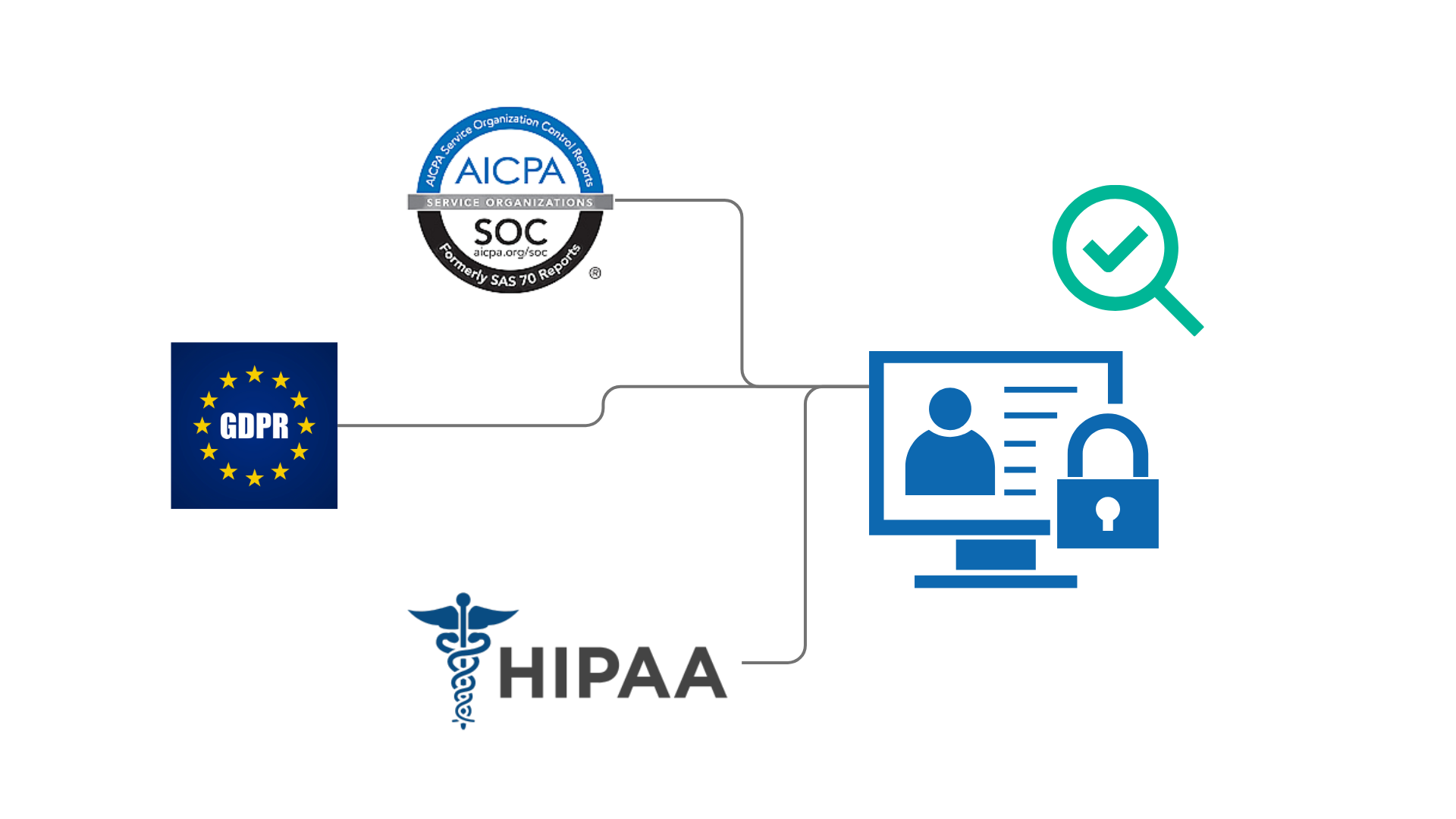
Certifications and Compliance
SOC 2 Audit to align with the highest standards of data security.
Fully compliant with GDPR, HIPAA, and other global privacy regulations.